Posted by: Wordpress Import April 14, 2014, 6:13 p.m.
So you exchanged your keys and revoked all corresponding Certificates? - Turns out you (and your sites visitors) are still vulnerable to MITM by stolen keys!
At least if your CA (like ours) lets your (and your sites visitors) Browsers cache their Certificate Revokation List (CRL) for up to 7 days.
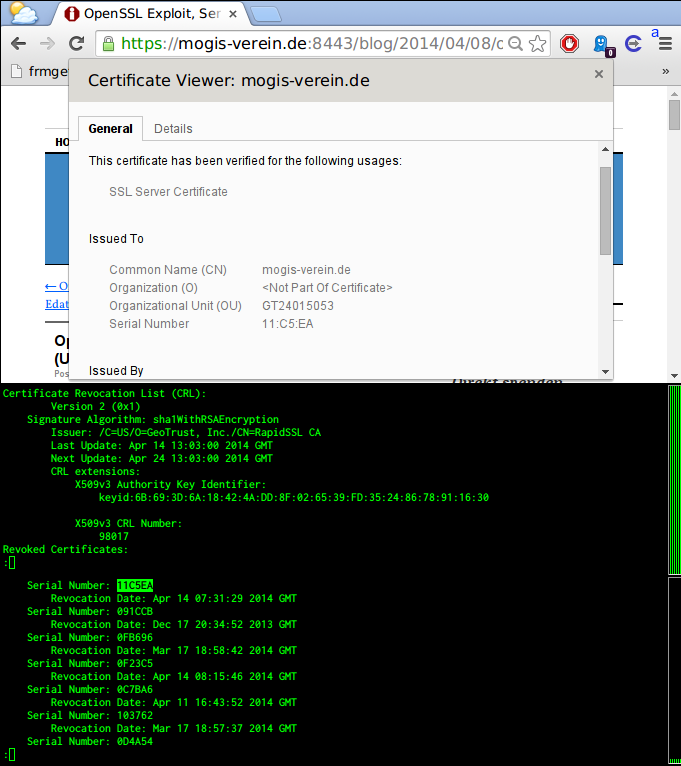
So even though the Certificate of https://mogis-verein.de:8443 is invalid, your browser will happily tell you it isn't.
So until the caching timeout for the CRL (that did non contain the revokations for our keys) comes around our site visitors are still vulnerable to MITM by the old (and probably leaked) keys.
Dear Rapid SSL, Thanks - for nothing! At least in this time of crisis you could have shortened the caching time to a few hours, so that certificates get invalidated faster
The relevant data:
Certificate Revocation List (CRL):
Version 2 (0x1)
Signature Algorithm: sha1WithRSAEncryption
Issuer: /C=US/O=GeoTrust, Inc./CN=RapidSSL CA
Last Update: Apr 14 13:03:00 2014 GMT
Next Update: Apr 24 13:03:00 2014 GMT
CRL extensions:
X509v3 Authority Key Identifier:
keyid:6B:69:3D:6A:18:42:4A:DD:8F:02:65:39:FD:35:24:86:78:91:16:30X509v3 CRL Number:
98017
Revoked Certificates:
...
Serial Number: 0F9083
Revocation Date: Apr 14 07:30:47 2014 GMT
...
Serial Number: 11C5EA
Revocation Date: Apr 14 07:31:29 2014 GMT
...
Recent Posts
- MOGiS e.V. in Expertenanhörung der Grünen/EFA im EU-Parlament am 28. März 2023
- #Chatkontrolle - Dorothée Hahne nimmt Stellung zum aktuellen Gesetzentwurf des Europäischen Parlaments
- Jahresrückblick 2022 und Spendenaufruf
- Offener Brief: Kinderschutz, Selbstbestimmung und Gleichstellung umsetzen: die "Beschneidungserlaubnis" § 1631d BGB abschaffen!
- Jahresrückblick 2021 und Spendenaufruf
Archive
2023
2022
- December (2)
2021
2020
2019
2018
2017
2015
2014
- December (2)
- November (1)
- October (1)
- August (1)
- July (1)
- April (3)
- March (2)
- February (3)
- January (7)
2013
2012
- December (5)
- November (2)
- October (3)
- September (15)
- August (3)
- July (6)
- April (1)
- March (3)
- February (6)
- January (2)
2011
- December (5)
- November (3)
- October (5)
- September (1)
- August (1)
- June (1)
- May (3)
- April (1)
- March (3)
- February (6)
- January (2)
2010
- December (1)
- November (5)
- October (3)
- September (6)
- July (2)
- June (1)
- April (6)
- March (7)
- February (1)
- January (2)
2009
- December (3)
- November (6)
- October (10)
- September (10)
- August (8)
- July (5)
- June (11)
- May (18)
- April (36)
Categories
- Netzpolitik (126)
- Pressemappe (84)
- In eigener Sache (109)
- Community (60)
- Betroffene (70)
- Offtopic (10)
- Uncategorized (34)
Authors
- Admin (3)
- Site Admin (15)
- Wordpress Import (258)
- Ben (3)
- We (2)